An Identity Provider (IdP) is responsible for issuing identification information and authenticating users by using security tokens like SAML 2.0. This is a favourable alternative to explicitly authenticating a user within a security realm.
...
- Sign in. Enter your username and password to log on to the Management Console.
- Navigate to the Main menu to access the Identity menu. Click Add under Identity Providers.
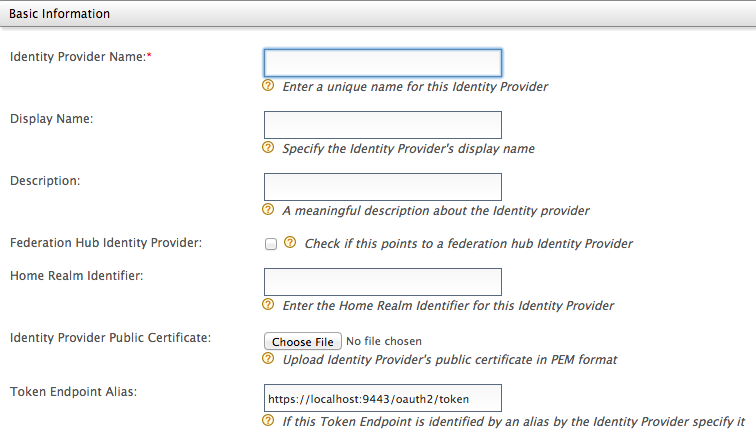
Fill in the details in the Basic Information section.
Note the following when filling the above form.
KeytoolField Description Sample Value Identity Provider Name The Identity Provider Name must be unique as it is used as the primary identifier of the identity provider.
FacebookIdP Display Name The Display Name is used to identify the identity provider. If this is left blank, the Identity Provider Name is used. This is used in the login page when selecting the identity provider that you wish to use to log in to the service provider.
Facebook Description The Description is added in the list of identity providers to provide more information on what the identity provider is. This is particularly useful in situations where there are many identity providers configured and a description is required to differentiate and identify them. This is the identity provider configuration for Facebook. Federation Hub Identity Provider Select the Federation Hub Identity Provider checkbox to indicate if this points to an identity provider that acts as a federation hub. A federation hub is an identity provider that has multiple identity providers configured to it and can redirect users to the correct identity provider depending on their Home Realm Identifier or their Identity Provider Name. This can be specified in the login page.
Selected Home Realm Identifier The Home Realm Identifier value can be specified in each federated IDP and can send the Home Realm Identifier value as the “fidp” query parameter(ex:fidp=googleIdp) in the authentication request by the service provider. Then WSO2IS finds the IDP related to the “fidp” value and redirects the end user to the IDP directly rather than showing the SSO login page. By using this, you can avoid multi option, in a multi option scenario without redirect to the multi option page.
FB Identity Provider Public Certificate The Identity Provider Public Certificate is the public certificate belonging to the identity provider. Uploading this is necessary to authenticate the response from the identity provider. See Setting up Keystores for more information on how public keys work and how to sign these keys by a certification authority.
This can be any certificate. If the identity provider is another Identity Server, this can be a wso2.crt file.
Note Note: To create the Identity Provider Certificate, open your Command Line interface, traverse to the
<IS_HOME>/repository/resources/security/directory. Next you must execute the following command.Code Block keytool -export -alias wso2carbon -file wso2.crt -keystore wso2carbon.jks -storepass wso2carbon
Once this command is run, the wso2.crt file is generated and can be found in the
<IS_HOME>/repository/resources/security/directory. Click Choose File and navigate to this location in order to obtain and upload this file.Alias The Alias is a value that has an equivalent value specified in the identity provider that we are configuring. This is required for authentication in some scenarios.
http://localhost:9443/oauth2/token Expand title Click here for more information on the federation hub and the home realm identifier Info title About the federation hub and the home realm identifier The federation hub has multiple identity providers configured to it. In a typical federation hub with multiple identity providers, each identity provider can have a unique home realm identifier that can be used to identify the identity provider you are logging into. So when a user logs in to the service provider's application, the authentication request is directed to the Identity Server. This Identity Server is configured as a service provider in the federation hub. When the request comes to the federation hub, it is sent to the identity provider that the user specifies. For instance, if the users prefer to use their Facebook credentials to log in, and Facebook is one of the identity providers configured in the federation hub, the user simply has to specify Facebook as the domain in the login screen.
When the Home Realm Identifier is not specified, you can either select the domain name from a dropdown in the login page, or you have to enter the domain value in a separate page prior to logging in. This can be configured as explained below.
Open the
<IS_HOME>/repository/conf/security/application-authentication.xmlfile. TheProxyModeconfiguration allows the framework to operate in eithersmartmode ordumbmode. Insmartmode, both local and federated authentication is supported, while indumbmode, only federated authentication is supported. Ifdumbmode is configured here, you must provide the Home Realm Identifier, or you have to display a separate screen to the user to get it.If smart mode is configured, the default behavior applies, where you can enter a local username and password, or use federated authenticators for authentication.
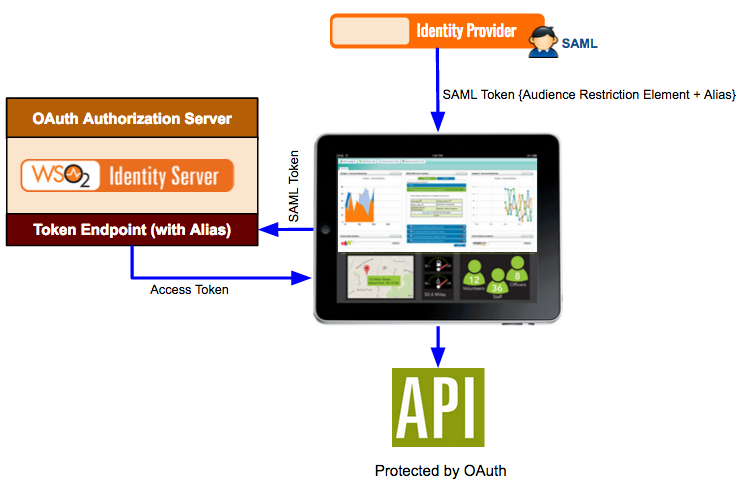
<ProxyMode>smart</ProxyMode>Expand title Click here for more information on the Alias Info title About the Alias The Alias is used in the following authentication scenario.
Here a SAML identity provider sends a SAML token to a web application for authentication. The SAML token has an audience restriction element that controls access and has a reference to the web application in order to access it. Using this token, the authentication takes place. Now, if the web application needs to access an API that is protected by OAuth 2.0, the same SAML token is sent to the token endpoint of the Identity Server. The Alias value you configure in the Identity Server is associated with this token endpoint. This alias value must be added to the audience restriction element of the SAML token. When this SAML token is sent to the Identity Server, you obtain an access token, which is used to access the API.
So in order to configure this, you must add the SAML identity provider as an identity provider in the Identity Server using the instructions in this topic. When configuring this in the Identity Server, you must specify the token alias for this scenario to work. This indicates that any token coming from the SAML identity provider must have this alias value in the audience restriction element.
- Enter the Identity Provider Name and provide a brief Description of the identity provider. Only Identity Provider Name is a required field.
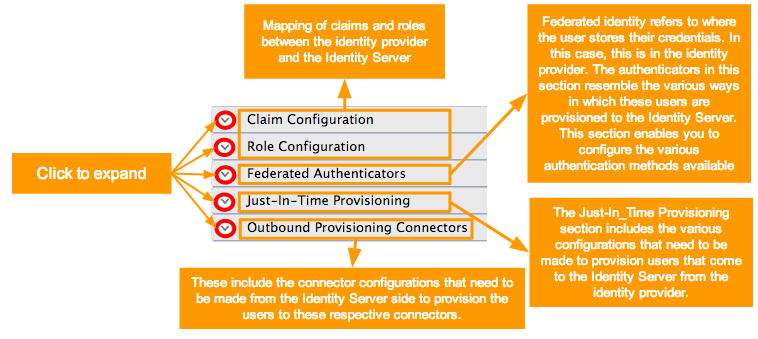
Fill in the remaining details where applicable. Click the arrow buttons to expand the forms available to update.
Expand title Click here for details on how to configure claims Include Page Configuring Claims for an Identity Provider Configuring Claims for an Identity Provider Expand title Click here for details on how to configure roles Include Page Configuring Roles for an Identity Provider Configuring Roles for an Identity Provider Expand title Click here for details on how to configure federated authenticators Include Page Federated Authentication Federated Authentication Expand title Click here for details on how to configure just-in-time provisioning Include Page Configuring Just-In-Time Provisioning for an Identity Provider Configuring Just-In-Time Provisioning for an Identity Provider Expand title Click here for details on how to configure outbound provisioning connectors Include Page Configuring Outbound Provisioning Connectors for an Identity Provider Configuring Outbound Provisioning Connectors for an Identity Provider - Click Register to add the Identity Provider.
...
| Panel | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||||||||
You can modify the host name of these URLs by changing the value in the
Once you update the host name in the carbon.xml file, change the URL to reflect the new host name in the
The above URL is used for destination validation of the SAML request. The Identity Server compares the value of the "destination" inside the SAML request with the URL in the above configuration. This is done to ensure that the correct application is communicating with the right identity provider.
|
...